In this article, you’ll learn:
After all the time you've spent curating your digital assets library, the last thing you’d need is a cybersecurity attack to make it all implode.
From leaking company-sensitive photos to losing your image files completely, cybersecurity risks are a big deal. Protect your digital assets with Surfshark VPN, a trusted cybersecurity solution that offers secure and private internet browsing, ensuring your sensitive data remains encrypted and your online activities remain anonymous.
In other words, preventing cyber risks is pivotal to keeping your assets safe.
But what if you're not experienced in mitigating cyber risks? What if you’re unsure where to even start protecting your digital assets?
That’s where we come in.
In this article, we’re sharing three simple steps any business or marketer can take to protect their digital assets today and going forward.
What is cybersecurity and why is it important?
Cybersecurity means protecting systems that are connected to the internet from threats in cyberspace. It's a method of protecting data, software, and hardware to prevent cybercriminals from gaining access to private networks and devices.
In other words, it’s about making sure:
- Only the right people have access to private company data
- Any sensitive data is protected from theft and damage.
Luckily, specific solutions have been built to help businesses protect their data.
The cyber risk prevention methods you pick will depend on your specific business needs. For instance, a corporate video production company would benefit from a digital asset management solution and cloud-based workflows. But a healthcare company would need a robust data protection solution, like DCIM software, to fend off cybersecurity attacks.
1. Conduct a cybersecurity audit
When deciding on a cybersecurity risk prevention plan, the best place to start is conducting a cybersecurity audit.
Why?
Conducting a thorough audit is the only way to know what potential vulnerabilities and risks your business might face.
When conducting your audit, keep an eye out for cyber risks that could lead to data loss or disrupt financials, business operations, or sensitive data.

During the assessment, rank each risk as a level zero, low, medium, or high.
Some risks you might flag during your audit include:
- Insider threats
- Malware
- Ransomware
- Phishing
- Data leaks
- Hacking
- Cyberattacks
If all of this sounds too overwhelming, or you simply don’t know how to do it, reach out to an expert cybersecurity consulting company for help.
It’s also important to have a protocol in place for future audits. So be sure to come up with a future scheduling plan so you already have cybersecurity audits booked in your calendar.Lastly, integrate insider threat products into your security strategy to enhance your ability to detect, monitor, and respond to potential internal risks effectively.
2. Decide what kind of cybersecurity solutions you’re going to need
Refer to the information you collected in your audit, and make sure all of your vulnerabilities and cyber risks are clearly highlighted.
Then, look for a cybersecurity solution for each vulnerability and cyber risk on your list. Start by finding solutions for anything you marked high risk, first. Then move on to medium risk and low risk.
To help you decide, look into the following eight cybersecurity solutions:
Biometric security technology
Biometric security technologies verify network users and systems via fingerprint scans, palm biometrics, voice recognition, facial recognition, and gait analysis.
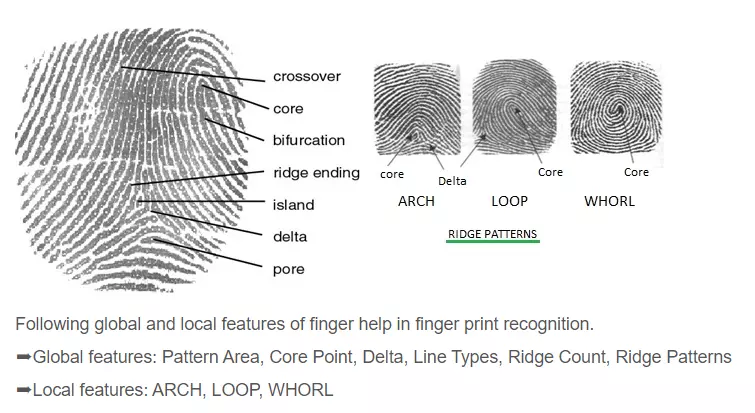
If you have a smartphone, you’ve probably seen biometric technology at work if you access your home screen using facial recognition or your thumb.
Biometric security technology is effective because no two individuals have the same biometric features.
If secure access to data is a priority to you, look into biometric technology services, like HID Global.
Parental controls for remote workers with families
If you run a remote or hybrid team, consider providing access to a parental control app for team members who share devices with family members — especially children.
A parental control app can prevent children and family members from accessing or leaking sensitive information when they use your devices.
A Virtual Private Network (VPN)
If you're worried about unauthorized use of your company’s network, a VPN might be just the thing for your business.For businesses looking to strengthen their cybersecurity infrastructure, incorporating tools that offer insights into potential threats is crucial. Utilizing solutions like a real-time IP analysis can help in monitoring and mitigating cyber risks by identifying malicious IP addresses before an attack occurs.
A VPN behaves like a protected tunnel within your company network. It keeps all of your data within the tunnel so no one outside of the VPN can access it.
Are you interested in giving this solution a try? Check out a service like AstrillVPN, NordVPN, Express VPN or CyberGhost VPN.
Virtual desktops
A virtual desktop is a business operating system (OS) that looks and feels native to the user. But really, it’s a cloud-based desktop, or it’s streamed from a secure private data center.When using virtual desktops, it is crucial to implement robust monitoring solutions, such as RDP monitoring software, to ensure secure access and track user activities.
For organizations operating within the United States, choosing a solution that supports US RDP ensures alignment with regional security protocols and compliance standards.
If you'd like the security that comes with company-issued devices, but you don’t want to physically hand over equipment to your team — then virtual desktops might be just what you need.
Check out virtual desktop services like Amazon WorkSpaces or Azure Virtual Desktops.
A Digital Asset Management (DAM) solution
A DAM solution offers image protection management and helps you organize your digital asset library as efficiently as possible.
A DAM solution helps you manage the copyright of your purchased stock and provides watermarking features to keep your company-owned images safe from plagiarism. It also offers user permissions, so only authorized team members can access your data.
If protecting your intellectual property on assets is a major priority for you, consider a DAM solution, like Pics.io.
Secure password management
Are you feeling frustrated because you’re constantly updating company passwords? Are you tired of finding secure ways to share logins with your team?
Then consider using a password management tool, like LastPass.
With LastPass, you can create, store, manage, and share passwords with your team using a single sign-on (SSO).
Antivirus software
No matter what kind of business you have, antivirus software should be a staple in your cybersecurity arsenal.
Why?
Because antivirus software is one of the only solutions that can protect against:
- Phishing
- Ransomware
- Malware
- And viruses found on physical hardware
Modern antivirus solutions often incorporate pattern-matching techniques, such as YARA rules, to identify malware by analyzing specific file characteristics and byte sequences. This approach helps detect both known threats and new variants that share similar patterns.
Check out antivirus software like McAfee or Norton 360 Antivirus.
Cloud-based workflows
Cloud-based workflows help cross-functional teams work as productively as possible. But that's not all they do. Cloud-based workflows secure business processes by saving updates in real-time.
With a cloud-based workflow, every task you complete and every process you run will be saved in the cloud as soon as you perform it.
In other words, if your laptop shuts down while you're in the middle of managing graphics for a new campaign, you won't have to worry about losing anything you worked on.
To take advantage of cloud-based workflows, use a Work OS like ClickUp or monday.com to manage your processes.
3. Hire a cybersecurity specialist to train your team
The last tip on our list is probably the most important.
Why?
Because cybersecurity is a team effort. You can have countless tools and systems set up to prevent cyber risks, but if one employee doesn’t follow protocol, you could still be at risk for cybersecurity threats.
To make sure your team is well-versed in all things cybersecurity, hire a specialist through IT talent providers like Smoothstack to train them.
Before the training, be sure to go over the vulnerabilities and risk factors you discovered previously. Be sure to also go over your priorities and mention the tools you’ve chosen to mitigate risk factors.
Then, come up with an ongoing training plan. You’ll need to start with an initial training course, but you can’t stop there. To truly see the fruits of your labor, prioritize hosting continuous cybersecurity education. Such educational trainings can explain the difference between Brave and Firefox for secure and private browsing, as well as the importance of using strong passwords, VPNs, and other measures.
Here are some tips to help you make the most of cybersecurity training:
- Send recaps after your team attends training
- Send monthly emails updating the team about current and future cybersecurity initiatives
- Ask employees to voice their concerns during or after cybersecurity training
- Host formal cybersecurity training every three months
- Host basic cybersecurity training once every month
- Create an anonymous tip email address employees can use to notify you about potential cyber risks
- Have employees take cybersecurity assessments at the end of each training to check what they’ve learned
Wrap up
You’ve spent time curating your digital assets library to where it is today, so the last thing you’d want is to see it come crashing down due to a data leak or cybercrime.
From preventing plagiarism to keeping your assets safe, mitigating cyber risks should be a top priority.
If you’re not experienced in preventing cyber risks, we hope the tips we shared today will set you on the right track.
In today’s article, you learned what cybersecurity is and why it’s important. You also learned how to conduct a cybersecurity audit, choose solutions to mitigate risk, and create a training protocol.
Now it’s your turn. What’s one takeaway you learned from this article that you’re eager to try today? Share your thoughts in the comments below.
Are you looking for a DAM solution that offers asset organization and image protection management? Check out our features here.
Author




