In this article, you’ll learn:
Imagine you've taken a beautiful photo or created a piece of art. To share it with your friends, submit it to a contest, or sell it, you publish it on the websites. At this point, you should consider all the details of copyright protection for digital assets and how to prevent copyright infringement.
Digital watermarking technology is a clever invention that quietly provides content protection in a digital world drowning in copies. We see them on money, certificates, stock photos, and videos. Yet most of us only notice them when we're intentionally looking for them. They're the quiet guardians of authenticity.
But what exactly is a watermark? Let's dive in.
What is a watermark?
A watermark is an identifying mark embedded into a medium—whether physical or digital—that indicates authenticity, ownership, or origin. The term comes from paper-making. Wire patterns create thickness variations in paper that become visible in light, resembling watermarks.
But that's the historical definition. Today, watermarks have evolved far beyond paper mills.
Digital watermarks can be either visible or invisible. Visible watermarks appear directly on visual files as recognizable marks, while invisible digital watermarks are embedded within the file's code without affecting how users see the content. Both types serve to establish ownership and deter unauthorized use.
In most cases, the human eye or ear perceives the digital content as unchanged. Specialized software can detect and read these hidden signatures. It works even after compression, cropping, or other modifications.
Types of digital watermarking
- Visible (overlay) — a semi-transparent logo/text on top of the image/video.
Example: a tiled "© AnnaStudio" across photo previews on your portfolio.
Use when: deterrence + branding for public previews and social.
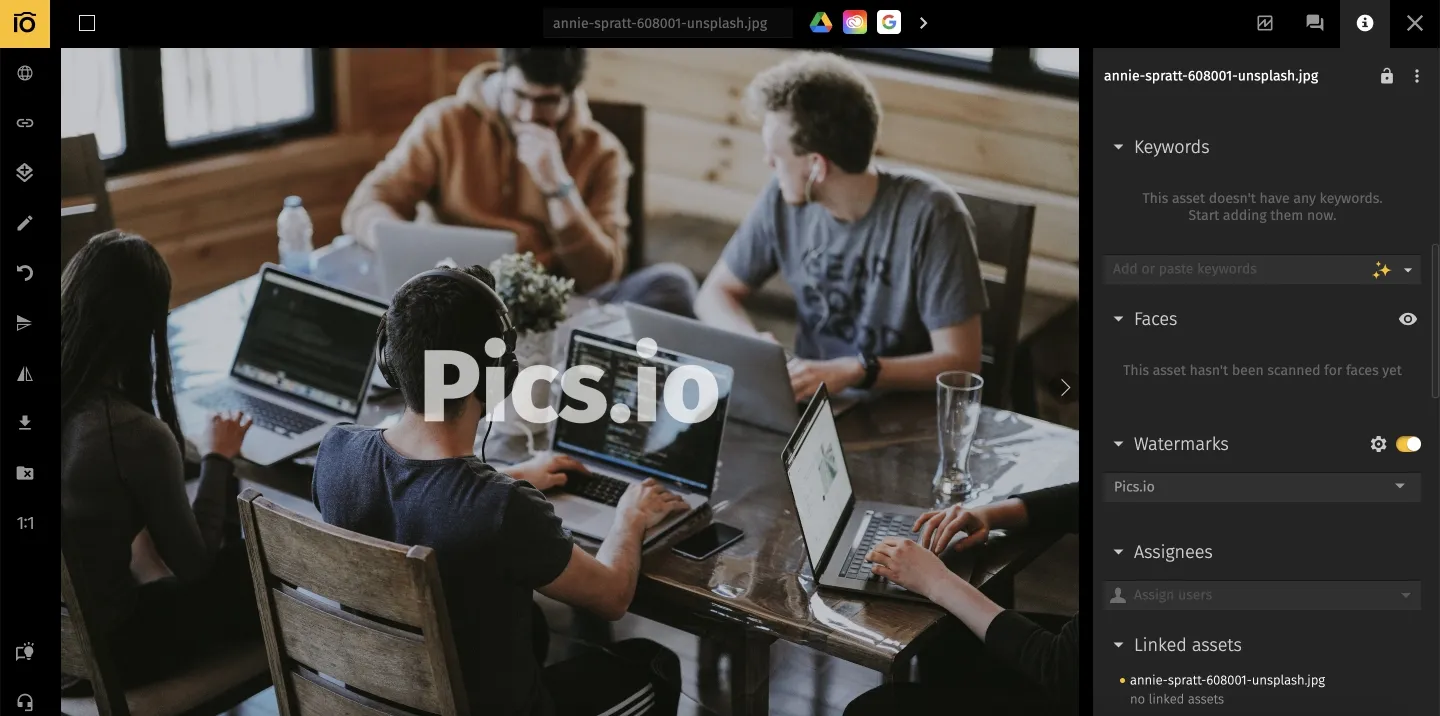
- Invisible – Robust (forensic) — hidden ID inside the media; viewers don't see it.
Example: every file a partner downloads gets a unique hidden recipient ID.
Use when: provenance/leak tracing that survives resize/compression.
- Invisible – Fragile — hidden tag that breaks on any change. These fragile watermarks are a type of digital watermarking technique used for tamper detection and content integrity verification.
Example: a PDF contract that flags "tampered" if a page is edited.
Use when: integrity checks (compliance, evidence, approvals).
It's pretty clear what a watermark is for — it warns other users about the copyright of a digital asset and the liability for its unauthorized use. But digital watermarking technology can also perform different functions, such as advertising the services of photographers and artists, promoting a particular brand, or even serving as an electronic seal for sensitive documents.
Who does it make life easier for?
Marketing teams: apply branded watermarks automatically before sharing visuals online. It ensures your content always carries your logo and protects against unauthorized reuse on social channels or by affiliates.
Communication and PR teams: use watermarks such as "Internal Use Only" or "Confidential" on press materials and draft assets to control what gets shared outside the organization.
Design agencies: automatically watermark preview images when clients are reviewing your work. Then give trusted clients a private link to download the clean, unwatermarked versions—no need to manually swap out files.
Video production: overlay watermarks like "Preview Only" or client names on rough cuts shared for feedback, so there's no confusion about which version is final or public-ready.
Educational institutions: protect sensitive visuals, charts, or student work with subtle watermarks before publishing online or sharing externally, helping maintain attribution and prevent misuse.
Content teams: add status watermarks like "Draft" or "Approved" to keep unfinished work from accidentally going live. It makes the approval workflow much clearer for everyone involved.
Legal and compliance: by limiting who can download unwatermarked files to specific roles, you significantly cut down the risk of intellectual property ending up where it shouldn't.
Key features of effective digital watermarking
Not all watermarks are created equal. If you want absolute protection for your digital assets, here's what matters:
Durability against tampering
A good watermark needs to hold up against the usual suspects: cropping, resizing, compression, switching file types, color tweaks, rotation—even some light Photoshop editing. That takes innovative technology. The best systems embed watermark data throughout the entire file rather than putting it in a single prominent place where someone could easily strip it out.
Imperceptibility
Modern technologies hide data within images without altering their appearance. They do this by understanding how the human eye perceives light, color, and detail, so the watermark stays hidden but still detectable by software.
Payload capacity
How much information can your watermark carry? A simple copyright notice? A unique identifier? Timestamp data?
Professional watermarking systems balance payload capacity against robustness and imperceptibility. More data generally means either more visible artifacts or less resistance to forging. Finding the sweet spot requires both technical sophistication and a clear understanding of use-case requirements.
Blind detection
Can you detect the watermark without access to the original, unwatermarked content?
Early systems needed the original image for comparison. It was impractical when scanning the internet for unauthorized uses. Modern blind detection algorithms can identify and read watermarks from any copy found in the wild, even after significant degradation.
Multiple watermark layers
Why pick just one type when you can use many? The most innovative approach combines visible watermarks and invisible watermarks. The visible one stops casual copycats, while the invisible one stays intact even if someone spends hours carefully removing what they can see.
You can even add multiple invisible watermarks, each serving its own purpose—creating a multi-layered protection.
Forensic watermarks
Top-tier systems use cryptographic watermarks that can do more than just prove the ownership—they can demonstrate an entire chain of custody. They are designed to detect tampering mathematically. If someone modifies the file, the watermark breaks in a detectable way, giving you concrete proof that the content's been altered.
Batch processing and API integration
If you're dealing with thousands or even millions of files, manually watermarking each one just isn't realistic. Professional tools offer batch processing, automated workflows, and API connections to your content management system.
The goal is to make watermarking invisible in your workflow—it should happen automatically when you upload or export files, without you having to lift a finger.
Cross-format versatility
The best watermarking solutions work across media types: images, videos, audio, documents, and even 3D models. Unified protection across your entire content library, managed from a single system, is far more valuable than disparate point solutions.
Popular file formats that have watermarks

PDFs are the workhorse of reports, contracts, and board packs thanks to their fixed layout and broad tooling support. Visible text/image watermarks are easy to add—but standard PDF editors also make them easy to delete. If you need tamper-resistance or user-specific IDs, look for workflows that protect the file at export (e.g., flattened layers, restricted permissions, or forensic IDs embedded at the data level) rather than a simple overlay.
Typical uses: "Confidential," "Draft," firm name/URL, per-recipient IDs for leak tracing.
Watch-outs: Basic overlays can be stripped; test removal attempts (edit, print to PDF, optimize/compress).
Microsoft Office (Word, Excel, PowerPoint)
In Word, you can add visible labels like "Draft" using the built-in Watermark feature. Excel lacks authentic watermarks—users usually fake them with headers, footers, or background images like "Not for distribution." PowerPoint uses the Slide Master to add logos or disclaimers across slides for consistent branding, not protection.
Good for: internal drafts, quick labeling, light "do not share" reminders, and consistent branding or disclaimers.
Limitations: easy to remove or edit; no dynamic, hidden, or per-user identifiers; not suitable for anti-leak or traceability purposes.
Google Docs
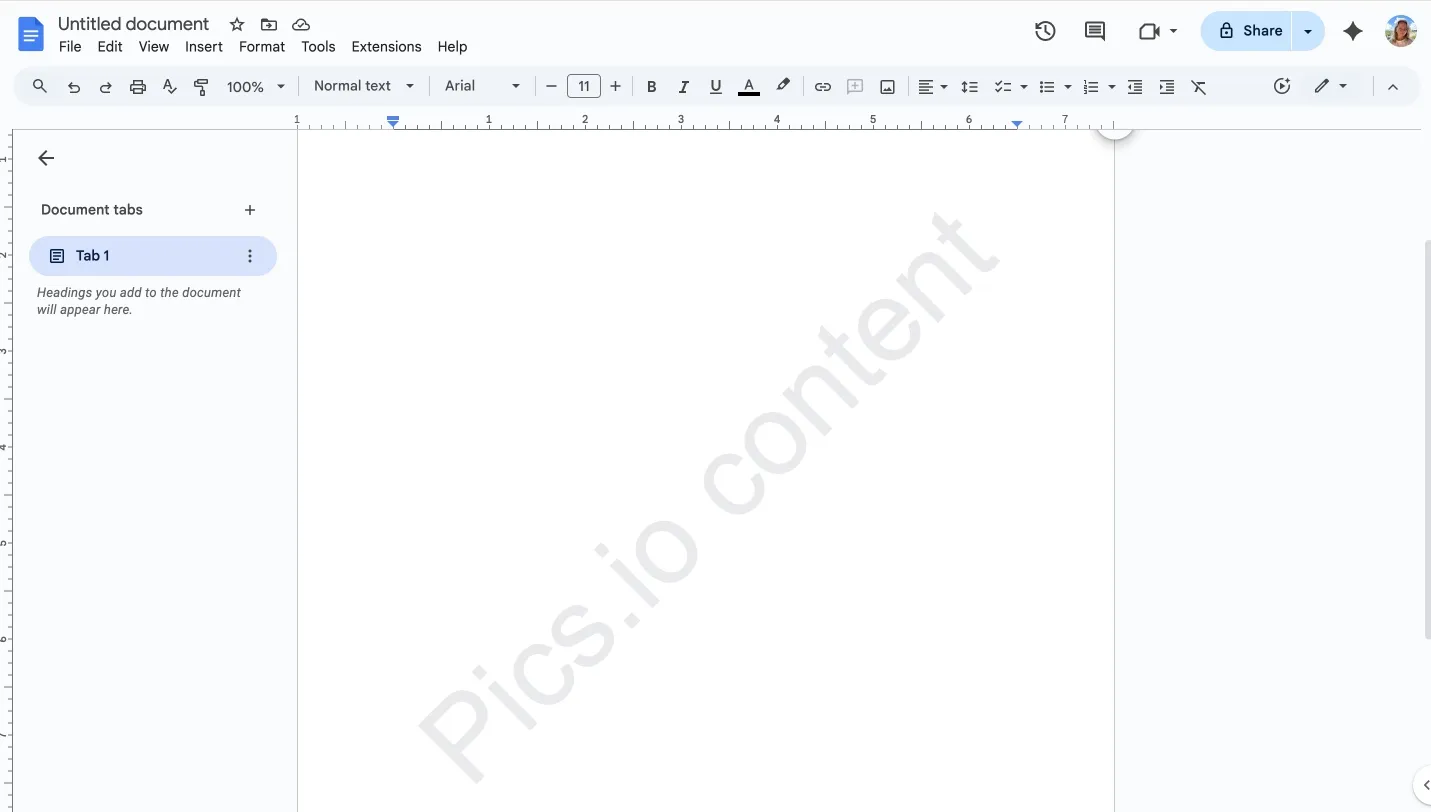
Docs supports image/text watermarks behind content and can restrict who edits them via sharing settings. That deters casual changes in the UI, but determined users can still work around them (copy content, export, reimport, etc.).
Good for: Lightweight, cloud-native labeling in shared docs.
Limitations: Workarounds exist; treat them as deterrents, not protections.
Video (YouTube, TikTok, etc.)
Most video watermarking is visible branding: a creator logo or subscribe badge. Hidden (forensic) watermarks exist—tiny pixel changes across frames to embed an ID—but face challenges.
Good for: Attribution on social, creator branding.
Photos and other images (JPG, PNG, GIF, WEBP)

Images are the classic watermark target—photographers, stock libraries, and designers rely on tiled logos or signatures. Professional tools (Photoshop/Lightroom) and batch exporters make this scalable. Invisible image watermarks exist, but, like video, they're sensitive to resizing, compression, and editing.
Good for: Public previews, portfolio protection, brand exposure.
Limitations: Modern AI/retouch tools can reduce or remove simple overlays; invisible marks may not survive heavy edits.
Audio (MP3, FLAC, WAV, etc.)
Audio watermarking can be impressively resilient. Techniques like spread-spectrum embed a barely detectable signal across a wide band; removing it without ruining quality is difficult.
Good for: Streaming provenance, leak tracing of pre-release tracks.
Trade-offs: Poor implementations can affect perceived quality—test before wide release.
Sheet music (digital distribution)
Publishers need legible notation and unique buyer identifiers. Visible marks mustn't obscure notes; subtle/invisible patterns risk being lost through photocopy/scan chains.
Good for: Buyer-specific labeling, print vs. digital policies.
Trade-offs: Balance readability with protection; offer opacity/placement presets.
Video games and other software
Watermarks occasionally tag screenshots or builds (e.g., per-tester IDs to enforce NDAs). Placement usually spans diagonals at low opacity to resist cropping. Determined users may still alter assets/configs.
Good for: Pre-release builds, NDA enforcement.
Limitations: May require additional controls (e.g., DRM and asset integrity checks) to prevent unauthorized removal.
Digital watermarking best practices
A watermark has to balance functionality and aesthetics. When applying digital watermarks to a digital asset, adhere to the following:
- Integrate the watermark directly into the file. HTML or CSS watermarks on web pages are easily removed by scraping programs. The embedding process should secure the watermark within the file structure itself.
- To increase protection, place the watermark in the center of the image or on its most informative areas. A good practice is to cover 40% of the image with a transparency of at least 50%. It makes it difficult to crop or remove without damaging the visual content.
- Add watermarks to the image corners only for branding purposes. Such elements can be easily removed by cropping or editing the image, thereby reducing their effectiveness as a means of copyright protection.
- Choose a contrasting background. A watermark in a monochromatic area of an image can be easily removed with basic software.
- Consider the file types you're working with. Different digital watermarking techniques work better for images versus videos, PDFs, or other document formats.
When to choose DAM over desktop tools for watermarking
Implementing robust watermarks effectively is essential, but when managing large volumes of assets, a DAM system offers additional control and efficiency. One common challenge is organizing multiple versions of the same asset — one with a watermark for distribution, another clean version for approved partners. Rather than maintaining duplicate files scattered across folders, digital asset management systems let you keep two versions in a single source of truth.
Permissions to remove or download files without watermarks are assigned at the role or team level, ensuring content security while maintaining workflow flexibility. This approach provides better access control and helps trace any unauthorized use.
So, choose a DAM for watermarking if:
- You regularly watermark hundreds or thousands of files and need to avoid repetitive manual work.
- You need unified presets and centralized control over who can remove watermarks.
- You need collaboration features, permission management, and download auditing for compliance.
How to watermark an image with Pics.io?
A digital asset management (DAM) system can be used as digital watermarking software. You can create custom watermarks and apply them to a single file or an entire file collection. Use the following instructions:
- Sign in to your Pics.io account.
- Go to My Team, then click Watermarking in the left-hand menu.
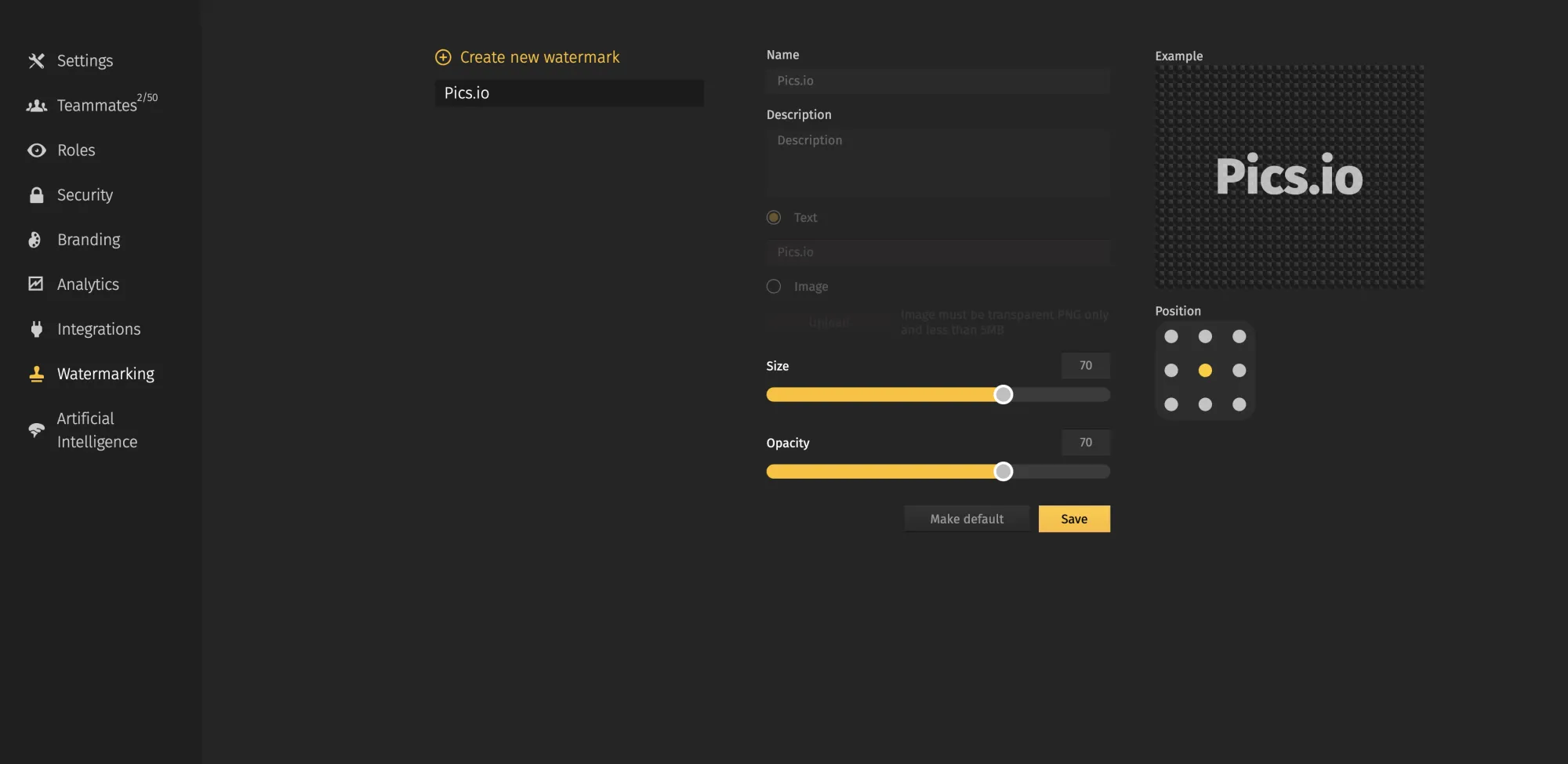
- Select Create New Watermark. Enter a name and description for the watermark.
- Set the type of security element — text or image (PNG with a transparent background, no more than 5 MB). Select the position on the screen, size, and transparency level.
- Save your changes.
- Find and select the digital assets you want.
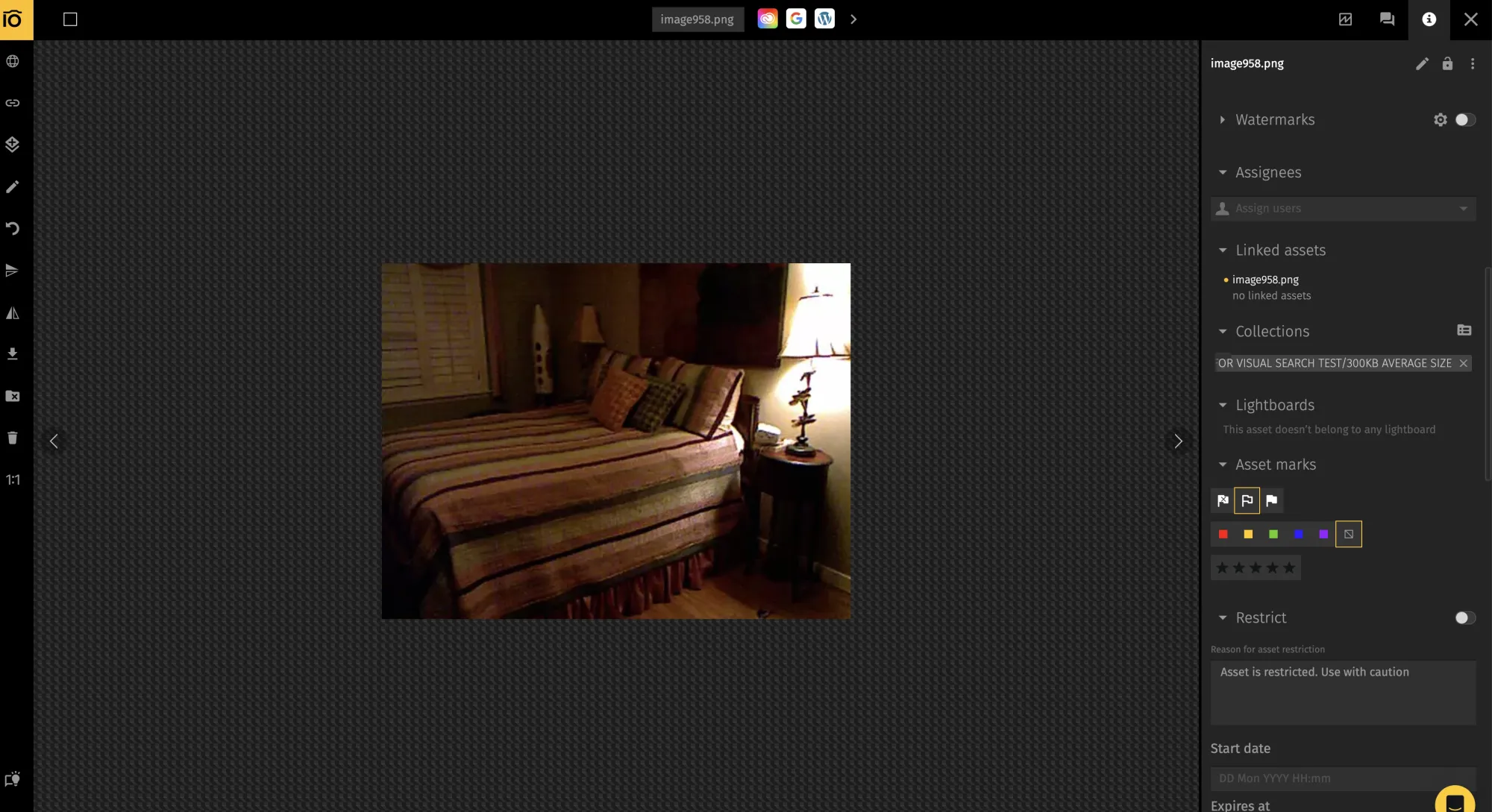
- In the Details panel on the right, select Watermarks and move the toggle to apply a custom watermark. It will automatically appear on all selected images. You can add watermarks to collections in the same way.
If you click the gear icon next to Watermarks, you can go directly to Settings to adjust your watermarks.

When uploading images to local storage, you can select the Download Without Watermark option to remove protection immediately.
The Pics.io platform also allows you to set permissions to remove watermarks and download files without them. You can learn more about supported formats and permissions in the Pics.io watermarking help article.
In addition to applying watermarks, Pics.io also helps you analyze file metadata to track authorship and usage. A watermark can reveal the image's owner or the platform it was posted on, but this information is often not enough to contact the author directly.
Conclusion
We've come a long way from that creamy paper in my grandfather's desk—from wire patterns in medieval paper mills to cryptographic signatures embedded in digital files. But the fundamental purpose hasn't changed: proving authenticity and protecting ownership in a world where copying is effortless.
Here's what I want you to take away from this: watermarking means professionalism.
The technology has matured dramatically. What once needed expensive software or hours of manual work is now possible with DAM systems, automated workflows, and smart algorithms. These tools balance protection with ease of use.
Visible watermarks deter illegal use while building your brand. Invisible watermarks survive the chaos of internet distribution. Forensic watermarks provide courtroom-ready evidence. Together, they create layers of defense that adapt to your specific needs.
FAQ
What's the difference between a watermark and metadata, and which should I use?
Metadata is information about the file stored in standardized fields, but it's trivially easy to strip. Watermarks, especially invisible ones embedded in the image data itself, survive these transformations because they're baked into the pixels.
Do I need expensive software to create effective watermarks?
No, for basic visible watermarks, you can use free tools. For professional workflows that process hundreds of images or for invisible forensic watermarks that hold up in court, you'll need advanced solutions, like DAM. Start with what you have, watermark consistently, and upgrade as your volume and protection needs grow.
Will watermarks affect my image quality or file size?
Visible watermarks are non-destructive overlays that don't degrade underlying image quality, though file size may increase by a few kilobytes. Professional invisible watermarks use algorithms that embed data in areas where human vision is least sensitive, resulting in no perceptible quality loss and a negligible increase in file size.
Ready to protect your content? Give Pics.io a try — or book a demo with us, and we'll be happy to answer all your questions.
Author
Eugene PristupaEugene is a Product Manager with deep expertise in Digital Asset Management (DAM) and workflow optimization. Holding a Master’s in International Economics, he combines analytical thinking with technical skills in frontend development and product analytics. At Pics.io, Eugene drives product strategy and innovation, shaping solutions that make managing digital assets simple and efficient.




