In this article, you’ll learn:
In 2009, the UK lost information on all prisoners when the USB in which the data was transferred became missing from an employee’s desk. Three years earlier, a laptop containing important information on over 26 million US veterans was stolen from the owner’s house. In 2007, a bug on DreamHost’s routers caused 500 websites to suddenly disappear from the web. And a few months ago, I lost important files gathered over four years while trying to fix a system error on my laptop.
These real-life examples are proof of the importance of data security. While data in previous generations was more prone to deterioration and damage, data in contemporary times is more vulnerable to theft, misappropriation, and devastating loss. Data security is perhaps one of the most important investments you can make, especially since information is now more centrally stored.
This article will share six simple ways you can protect your content and ensure that your data is secure always.
The things we keep
People store just about anything; here’s a list of commonly stored content:
- Personal files: these image, video, audio, and text files include, family photos, vintage music catalogs, manuscripts, contracts, family videos, birth certificates, marriage certificates, educational credentials, professional certifications, etc.
- Financial information: bank account details, credit card information, internet banking login credentials.
- Corporate data: business transaction details, contracts, employee information, client information, payroll data, proceedings of business meetings.
- Web content: this includes site themes, content, and settings.
Data storage: Where to Keep Them?
The choice of data storage is dependent on access to technology, affordability, cyber security consciousness and the size of your data. Here’s a list of popular storage locations:
- Safety deposit boxes
- Storage units
- Compact disks
- USB sticks
- Computer hard disks
- External hard disks
- The cloud
- Network attached storage
Prowlers on the move: How secure is your data?
Information is powerful and for many can be deeply personal. Hackers know this, they capitalize on the fear of loss to not only threaten your security but breach it to carry out malicious intent or sell it to the highest bidder.
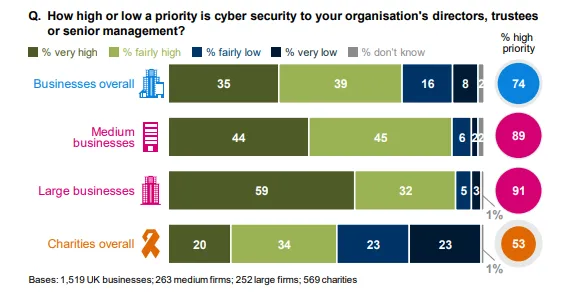
The first step to securing your data is being aware of the reality of data theft, the various forms it can take, and the role that cyber security plays. Here’s what a 2018 survey revealed about the importance of cyber security for businesses and charity organizations in the United Kingdom.
Six simple ways to protect your data
1. Take care of your passwords and monitor your account settings
According to a research, 37% of credential theft was due to weak passwords. So what makes up a strong password? It should have:
- Letters
- Numbers
- Special characters
- Capital letters
- Small caps
- At least eight characters
Your password should be private, this isn’t something you scribble on a scrap of paper or ask someone to advise you on. Make sure it is something you can easily remember and that you change it often—experts recommend that you do this four times a year.
With so many websites and apps requiring a password, it can be hard to keep track of them all. Google Password Manager offers a secure password management system that not only secures your password across several devices, but also helps you to generate stronger passwords and monitor their usage elsewhere. While this is a great idea, it can be disastrous if your device ends up in the wrong hands—stolen or not. So there are three things you can do: make sure you can easily remember them, write them down somewhere safe, make sure your device is absolutely secure—if that’s actually possible.
If multiple users have access to your social media account or website for work purposes, you should ensure that they are of unquestionable character. A simple online background check and asking the right questions during the recruitment process will suffice. Behavioral questions will give you an insight into their personality and what you can expect them to do in real life situations. You should also take advantage of your administrative controls to ensure that they have limited access and cannot hijack your website or account.
Another great way to secure your content is to enable a two-factor authentication that prevents hackers from easily hacking your devices if they have been stolen.
Finally, it's important to understand that the weakest point of every system are actually people. Social engineering and similar frauds are used to acquire in-house information that is later used for cyber attacks. Ensure that your employees are regularly undergoing IT security training on a regular basis.
2. Avoid public Wi-Fis and keep personal information private
Who doesn’t want free Wi-Fi, especially when you desperately need to make a call, use Google Maps, or make a quick payment? In an age where we’re increasingly dependent on technology for communication, it seems that you must be constantly connected to the internet, whether the access to it is free or paid for. However, connecting to public Wi-Fis can open you up to hackers who harvest information from unsuspecting users. If you do not have a data connection, make every effort to connect to a trusted Wi-Fi or use other traditional means of communication.
So much havoc can be done with access to your personal identifiable information such as: your birth date, full name, email address, social security number, and passport number.Therefore, you should be cautious and ensure that any entity requesting such details implements proper Name and SSN verification processes. So you should be frugal with the type of personal information you share, especially in places with no clear information on how your information is used, stored, and distributed. Restrict information sharing to places where your information is respected so that your content is not compromised.
If you choose to shop online, do so on websites that are secure. Look out for the padlock icon on the top left corner of the address bar—this shows that the website has a SSL certificate. The SSL certificate authenticates the website and encrypts any interaction with the website. Shopping on insecure websites can leave you open to hacker attacks that can compromise your private content. Besides, if you are a website owner then, a strong SSL certificate should be there on your website. For that, you can go with a single domain or buy wildcard SSL for website security. Many providers are there who can offer you handsome discount on your SSL purchase. It will save your cost also.
Another way to protect your content is to regularly check your device’s permissions, to see how much access apps have to your content. Sometimes, it’s easy to miss these permissions—you may have overlooked them at the time of installation. This is all part of understanding that there are multiple attack surfaces via which malicious actors can target your content. There's lots to be aware of, from the devices you use to the networks you connect to, and beyond.

3. Backup your data—do it today
It’s hard to predict certain events, such as when your device can crash, be stolen or damaged. This is why it’s important for you to back up your data, and you can do this using an external hard drive, or simply store it in the cloud. Google gives you free storage of up to 15 GB, after which you can purchase more storage space up to 2 TB. Other popular cloud storage providers include Dropbox, iCloud, and OneDrive.
It’s hard to predict certain events, such as when your device can crash, be stolen or damaged. This is why it’s important for you to back up your data, and you can do this using an external hard drive, or simply store it in the cloud. Google gives you free storage of up to 15 GB, after which you can purchase more storage space up to 2 TB. Other popular cloud storage providers include Dropbox, iCloud, and OneDrive.
Another trick to backing up your file is storing it in several places. So for instance, you can store your files on your computer’s hard drive, on an external hard drive, or a USB stick. You must however ensure that these locations are safe from theft or damage. If you or your business have heavy content that you’re struggling to control, then a digital asset management software such as Pic.io is the key to keeping you in charge of all your information.
Working on top of your storage like Google Drive or Amazon S3, Pics.io helps you manage & distribute your data in case your digital assets outnumber 500+. This DAM solution can also help businesses to secure their data. For example, with Pics.io, business owners can restrict sharing some assets or distribute roles between users right. So some people will manage your media library, while others will have view-only rights.
Backing up your website data is also important; you will save yourself from data loss and a ton of regret. If you can’t keep track of the updates—especially if you’re using a content management system like WordPress—then you should schedule updates to automatically backup your site’s data. If you don’t already do this and you need to make changes to your website, it is advisable that you backup your site content before you execute these changes. If you don’t like the new changes, it’s easy to restore your website to the previous settings, if you can retrieve an earlier version of it. You will likely have to rebuild from scratch if you can’t locate this backup, and how sad and time-consuming that will be.
4. Avoid Dangerous Apps and Clickbait
Earlier this year, Better Business Bureau sent out an alert about scammers who might take advantage of Kobe Bryant’s death to lure unsuspecting fans, using clickbait. This is just one of the examples of links that are really a front for phishing attacks. Another example is Google’s claim of blocking over 100 million phishing mails, a portion of it linked to the coronavirus.
Look for news on credible sites you’re already acquainted with. Don’t go looking for odd news where the webmaster’s intent is to lure you in and steal your information. These clickbait are usually sensational: Man grows two extra fingers after eating a giant pork sandwich. I know, it sounds intriguing, but I guarantee you, your safety is more important than a peculiar story.
Don’t be eager to click that game or quiz app that asks you for personal information. Most of these questions are asked in an engaging manner and give fun rewards for participation, but don’t be fooled. These apps have malware that lurk in your device, fishing for private information and content.
You should also avoid clicking on suspicious links in your email, you’ll usually get a warning telling you that the email source seems suspicious. Send it straight to your Spam folder.
5. Get an effective antivirus
Even if you’re using the free version, you should get an antivirus that at least provides a firewall for your device and web and email activities. Advanced features usually include protection from hackers, privacy protection and payments protection. Most subscriptions allow you to enjoy protection on at least two devices, so you can be sure to have protection on your devices. This is especially important if you own a small business and are trying to secure your internal business communication from prying eyes.
The best antivirus software provides security from viruses and malware that can corrupt your documents, slow down your system and make your content inaccessible.
6. Be cautious on online forums
If you are a content developer, it is likely that you are in a social media or online community. In these groups, participants often share content ideas and even finished works, and because of the nature of the job, you are likely to seek feedback and collaboration opportunities. However, there is the high risk of intellectual theft on these forums.
Here’s what you can do to protect your content even when you’re online:
- Sign a non-disclosure agreement before you share your content with anyone
- Only be a part of online forums where there is a strict policy on intellectual property rights and usage
- Don’t share your content if you don’t trust the receiver
Final thoughts
These simple tips take a conscious effort to ensure that your content is safe. Don’t let your guard down for a moment. One security breach can unleash a nightmare you never imagined. One more thing to note: ensure that your device is in safe hands. While you may make all reasonable efforts to protect your content, it can all be in vain if the wrong person is mishandling your device, sharing your content without your approval or using it for their own purposes.
In a nutshell, here are the simple ways to protect your content:
- Take care of your passwords
- Avoid public wi-fis and keep personal information private
- Backup your data today.
- Avoid dangerous apps and clickbait
- Get an effective antivirus
- Be cautious on online forums
Above all, go with your gut. If you feel uneasy about sharing your content somewhere, don’t.
And if you're looking for an excellent digital asset management solution – Pics.io is the right tool for you. Store, organize, & distribute your files the most productively.
Author




